By Ben Cruikshank, Sam Millar, & Cameron Wells
Introduction
Data breaches are a company’s worst nightmare, yet surprisingly, scrambling, or anonymising non-production data is still startlingly rare. In this blog post, we’ll explore the power of data scrambling – a simple yet effective technique to reduce the chances of data breaches while maintaining data usability in a non-production environment. We’ll delve into what data scrambling is, why you should scramble your non-production data, how scrambling can protect your data, and how our expertise can assist you in safeguarding your valuable information.
Background
When changes are required within an IT solution, such as a website, software or even a data analytics solution, a development environment, often called a non-production environment, is used, so changes can be made without affecting the live (in-use) environment until those changes have been tested, accepted and then safely deployed. Changes are usually deployed to the live environment during a clear window when it has the smallest risk of disrupting users.
These non-production environments are usually accessible to a range of developers and testers to perform the development of the environment. These non-production environments have less protections of data around them. Such as:
- There’s less security applied, so they are easy to access, change and test
- Environments exists in a less secure infrastructure
- Environments may be accessed by third parties in foreign countries
Unfortunately, it is very common for real data to be copied from a production environment and placed into a non-production environment. This raises a swathe of concerns around data privacy and protection as it is highly vulnerable to being accessed by unauthorised people. We highly recommend that any data used within a non-production environment is scrambled so it is no longer real.
What Is Data Scrambling?
Data scrambling involves masking, removing, altering, and anonymizing sensitive data in a manner that makes it irretrievable. Here’s how the process works in a nutshell:
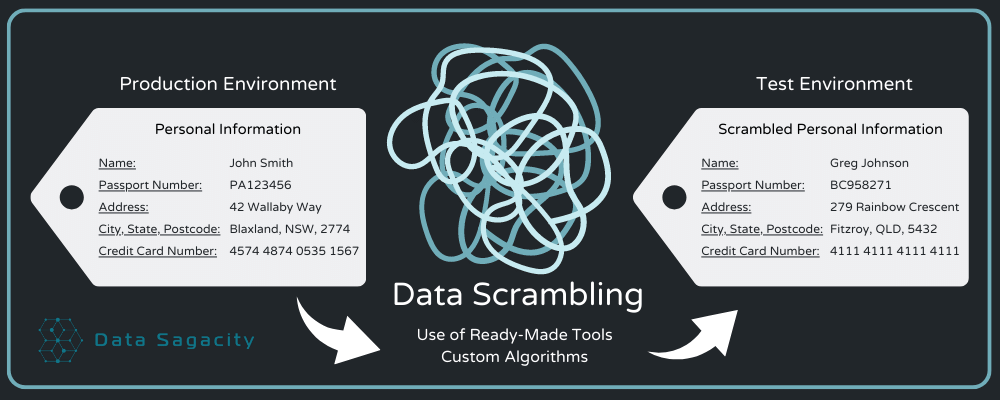
Scrambling is done in a variety of ways depending on how the data is stored and secured but here’s some of the main techniques:
- Tokenization: Replacing sensitive data with tokens or placeholders.
- Obfuscation: Modifying data to make it harder to understand or reverse engineer.
- Salting: Adding random values to passwords to enhance security.
- Data Masking: Replacing sensitive data with realistic but fictitious information.
Why Should I Scramble My Data?
In short, to reduce any kind of unnecessary access to sensitive data, whether its authorised or not.
Scrambling or desensitizing production data helps balance data utility with the protection of sensitive information. It addresses privacy, security, and compliance concerns in various contexts. Here’s some more specific use cases:
- Data Privacy and Compliance: To comply with regulations and protect customer information, sensitive data needs to be scrambled or desensitized.
- Testing and Development: Anonymizing or altering data while maintaining its structure creates realistic test and development environments. It enables developers and testers to work with representative data without exposing sensitive information.
- Outsourcing and Third-Party Access: Protecting data when sharing it with external partners or vendors minimizes the risk of unauthorized access or misuse. By scrambling the data, it can be used for analysis or development while safeguarding confidential information.
- Training and Education: Ensuring privacy in educational settings while providing valuable resources for students or researchers is possible by modifying sensitive data. Anonymization allows for learning opportunities without compromising individuals’ privacy.
- Data Analysis and Research: Utilizing scrambled data can be valuable for conducting data analysis or research studies focused on general trends rather than specific details. Anonymization techniques enable meaningful insights while protecting privacy.
How Can Data Sagacity Help?
At Data Sagacity, we specialize in data security and privacy solutions. We have developed our own automated data scrambling process, ensuring efficient and effective implementation of data scrambling techniques. This process enables us to seamlessly transform sensitive data to develop valuable insights while protecting the data of our clients.
To see an example of our scrambled data in action, head over to one of our client’s websites API Integrations. Here you can check out reports and get a feel for how data looks after going through our data scrambling and desensitisation processes.
So, if data security and privacy are your concerns, Data Sagacity is here to help. We’ve got the know-how, the automated processes, and the cool mock reports to give you peace of mind. Your data will be safe in our hands.